Cryptographic hashing is the process whereby a mathematical function is used to generate values from a string of text.
In essence hashing is a type of encryption process. It involves some form of data being inputted, which is transformed into a string of values that can only be decrypted with the permission of the owner of the information. The string of text that is produced by hashing is called a ‘hash ‘value.’ There are currently eight main hash algorithms, MD5, SHA-1, RIPEMD-160, Whirlpool, SHA-2, SHA-3, BLAKE2 and BLAKE3. The Bitcoin (BTC) blockchain utilizes the SHA-256 hash algorithm.
What is a Hash Rate?
The hash rate or ‘hashrate’ is the total number of nodes (computational power) being used by a cryptocurrency blockchain network to produce proof-of-work (POW) algorithms while processing transactions. This is calculated on a per-second basis, meaning how many total calculations can be processed by the collective processing power of all of the computing nodes in that network each second. These transactions are either in the form of encrypting, decrypting, or transferring data. The amount of computing power required for POW depends on the hashing algorithm. This also affects the amount of time that it takes to decrypt the code.
What is the purpose of hashing?
The first purpose is for storing passwords. Although it is extremely easy for a hash to be calculated or any given data, it is extremely computationally difficult to then calculate the original alphanumeric text that has been given a hash. This graph below was provided by Reddit user u/hivesystems to illustrate the difficulty that a single computer would have in cracking passwords of various lengths and number/letter combinations:
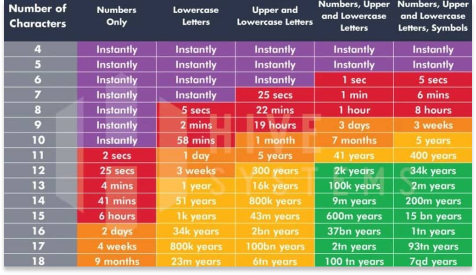
Obviously, the color-coding should be ignored for this table. However, one reason for the possible discrepancies is that it is based on current technologies. After all, even 0 years ago, current computing capabilities were unfathomable, and yet even the cheapest smartphone can compute at greater rates the best computers of 1961, when the 7030 Stretch supercomputer was first produced by IBM and considered to be the pinnacle of computing at the time as the first 64-bit computer in the world. Yet now, it is not uncommon for a high-end mobile phone to possess a 64-bit chip, and as we said above, the highest possible code length of the SHA-256 algorithm is 256-bits. Therefore, from this table we can see the value in a decentralized encryption process that can hash such large and varied hash values towards ensuring greater security and data protection.
The second purpose of hashing is integrity verification. This entails the computer comparing a files hash value to its previously calculated value in order to ensure that it has not been corrupted. It even one value in the string is different, it means that it has either been corrupted or is the incorrect file.
What is a bit?
‘Bit’ is an acronym for ‘binary digit.’ It is the smallest increment of data in computing. A bit can hold only one of 2 values, namely either 0 or 1.
What is a bit in SHA-256?
“SHA-256” stands for “Secure Hash Algorithm 256-bit.” Therefore, it is an algorithm that is capable of hashing a code that is up to 256-bits long, meaning that it would produce a string of 256 0s and 1s. The way in which the bits are arranged is what gives them meaning. In the case of the SHA-256 hash algorithm, it generates random numbers in a way that requires a predictable amount of computer processing power, namely 10 minutes.
How does the SHA-256 algorithm work?
In order to ensure that this hash rate is consistent, the algorithm will automatically adjust the mining difficulty according to the number of nodes (computers) involved in the hashing process. It does so by producing a code that is a number between 0 to 256-bits long, again, depending on the number of nodes involved. All of these nodes will work at computing possible solutions to the algorithm until one eventually gets the hash value. The number of computations that all of the nodes processed while attempting to crack the code is the hash rate for the algorithm. Once the code is solved, the code is locked, meaning that the block is finished and the node that successfully ‘guessed’ the hash value will be awarded BTC. The rest will need to try their luck again with the next block. This process of attempting to acquire coins for successfully calculating the hash value is referred to as ‘mining.’